Comodo has world class software engineers in our R&D offices in the US, UK, Eastern Europe, India and China. Our operations glean real world data that our R&D centers around the globe leverage to make you safe:
- Whitelist (Known Good): Comodo CA knows all the publishers and produces a comprehensive list of known valid files for our scanners.
- Blacklist (Known Bad): Comodo AV labs: knows the malicious files that our users are encountering and maintains a signature file of known files threats that is second to none.
While our Whitelist and Blacklist are second to none, what is makes us extraordinary are we do not stop with detection based on what is known. We have solved the riddle of how to deal with the unknown!
Conquering the Unknown
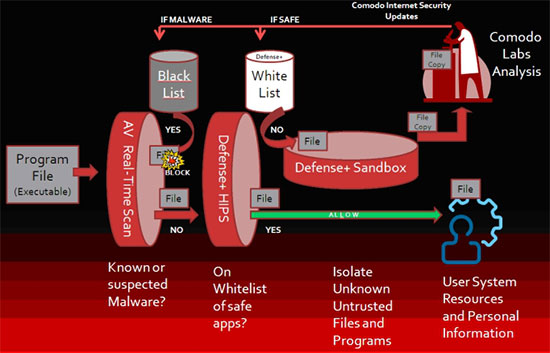
Conventional protection can deal appropriately with files that are known to be good and those known to be bad. Unfortunately, they do not have an adequate solution when confronted with the vast number of files that do not fall neatly into either category, unknown files.
A percentage of these unknown files are malicious. After all, an estimated 50,000 new malware threats are unleashed don the world each day. Your scanner will not know all of them.
If your default is to allow unknown files to run, eventually one will harm the system. That's why conventional protection fails. It can't repeal the laws of probability. The percentages will catch up to you eventually. Malware will infect your system if you use it long enough. That's the simple truth.
Default Deny with Auto-sandboxing
The Jail House Method of Containment
We understood that simple truth and created a new paradigm we call "Default Deny". Such unknown files are denied access to your system and files. The unknown files that are malicious can never harm you.
We understood that simple truth and created a new paradigm we call "Default Deny". Such unknown files are denied access to your system and files. The unknown files that are malicious can never harm you.
Application Isolation
The Fortress Method of Containment
We developed Default Deny with Auto-sandboxing to protect desktop users and organizations endpoints and to keep them from ever becoming compromised.
However, a large customer of ours came to us with a different challenge. They need to operate a financial application on customer endpoints that they do not own and control, as many as 400,000 desktops. They assume that many of these desktops will already be infected by malware and compromised by hackers, but the application must still operate safely.
What they were asking for is the digital equivalent of a Navy Seal who can enter a hostile environment, get the job done and exit without casualties.
Sound like Mission Impossible?
Not to Comodo's R&D engineers, who have developed an extraordinary application that allows you to run your critical application, such as POS System, safely when the platform has already been compromised.
This is what we call securing a Good file in a Container operation in a Bad environment. But we can also contain a Bad (or unknown) file operating in a Good (clean) environment and keep a device clean!
Comodo technology can be configured to match your unique threat scenario like a child puts together Legos to create unique designs. We like to call our security technology "Lego Land" because Comodo R&D engineers can mix and match our technologies to create unique solutions to specific challenges. They are given license to tackle and solve the problems based on what they observe in the real world.
That's what makes us special, the ability to solve problems that others have not even identified yet and to confront and conquer the unknown threats that others fail to do.