What is a Ransomware Attack?
Ransomware is a type of malicious software that encrypts a user's files so they cannot be opened without a decryption key. The criminal will then demand ransom money in return for the decryption key. The encryption algorithms employed in ransomware are typically on the higher end - AES + RSA encryption with RSA(426)-AES and RSA(1024)-AES, and RSA 4096 keys. For all intents and purposes it is impossible to decrypt these files without the correct key. Often, companies and individuals have been forced to pay the ransom money to get their files back - though payment does not always ensure receipt of the decryption key.
The ransom is demanded in the form of bitcoins, online cash, Amazon gift certificates, premium text messages, or wired through Western Union. The extorter usually demands that the victim pays up within a specific time-frame or certain parts of the data will be destroyed. They may also warn that the price of decryption will increase with each time the payment is delayed.
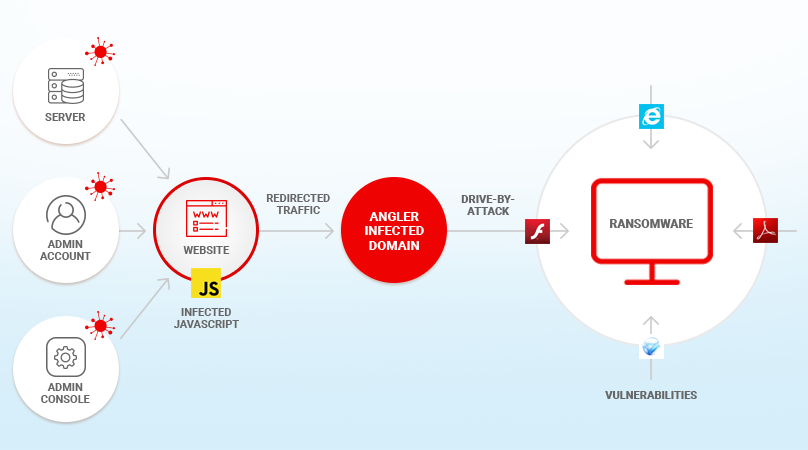
How to Protect Against Ransomware Attacks?
Comodo offers comprehensive protection against ransomware through Comodo Endpoint Security Management (CESM) for enterprises and Comodo Internet Security (CIS) for desktops and laptops. Ransomware has been introduced in many variants. Attacks by well-known ransomware can be prevented as the malware's signature will have been added to the databases of major antivirus companies. But how do users protect themselves against brand new, zero day ransomware? New ransomware is 'unknown' to a traditional antivirus scanner until it has been detected and proven to be malicious by an unfortunate victim.
Traditional Antivirus products are ineffective against ransomware as they basically follow a detection-only approach as their first line of defence. This means the ransomware has to infect somebody before it can be classified as a threat. Obviously this is not effective protection. Nobody should have to sacrifice themselves by being infected and extorted before a solution is provided. Comodo Internet Security beats even zero-day ransomware with a default-deny approach and containment system. All unrecognized processes and applications - which could be zero-day exploits - are automatically run in a secure container where they are not allowed to access a user's files and data. While contained, the behaviour of the unknown process is heavily monitored for harmful activities and, crucially, cannot access or infect the rest of the computer. If behaviour testing finds the file to be malicious it will be immediately quarantined.
How to Prevent Ransomware?
Comodo Containment Against Ransomware
Comodo Endpoint Security and Internet Security protect you against ransomware by preventing it from ever accessing your file system. Unlike other security products Comodo Endpoint Security and Comodo Internet Security effectively protect against zero-day exploits and ransomware through containment with auto-sandboxing.