Designed for organizations requiring centralized administration of their server and desktop security, Comodo Endpoint Security Manager harnesses Comodo's core threat containment technology to set a new benchmark in endpoint management and security.

Combining the short learning curve of Comodo's award winning security suite with real-time visibility over critical system information, ESM is the single-pane-of-glass through which enterprises can gain insight and control over all network endpoints.
- Multi-layered defense offering integrated Virus Protection, Firewall , Auto-Sandbox, Host Intrusion Protection, File Reputation Lookup and Behavioral Analysis
- Unique, persistent, fully-automated Sandbox executes 0-day and other untrusted files in a contained environment - allowing Comodo to be the only vendor offer a $5,000 virus-free warranty
- Centralized administration of all Quarantined, containerized or unrecognized applications provides ‘one-click' administration of threats
- Management UI displays 14 critical metrics required by the administrator for ‘first-glance' alerting and remediation of LAN and WAN managed systems
- Direct endpoint visibility and control allows management of endpoint processes, services, installed applications, resource usage, removable devices and power usage
CESM combines our core containment architecture with best-of-breed blacklist and behavior based detection, an industry recognized firewall and the whitelisting engine of Defense+.
CESM's contain, diagnose and protect technology defends systems from potentially malicious executables by containing unrecognized applications and excluding them from OS interaction.
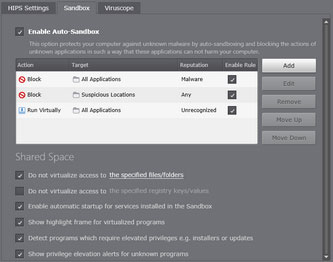 After an untrusted application has been contained, it passes through another layer of defense - File Rating. The executable is automatically uploaded to COMODO's malware analysis laboratory and undergoes a battery of automated and manual tests in order to determine whether or not it is harmful.
After an untrusted application has been contained, it passes through another layer of defense - File Rating. The executable is automatically uploaded to COMODO's malware analysis laboratory and undergoes a battery of automated and manual tests in order to determine whether or not it is harmful.
If it is determined to be malware, a virus signature is created for it in near real-time and added to the signature database. If the verdict isn't sufficiently positive or negative then the application will continue running in the Auto-Sandbox until the administrator either creates their own whitelist rule or deletes the executable.
Proactive ManagementComodo Endpoint Security's user-friendly policy creation wizard can generate and enforce administrator's configurations within minutes. Policies allow administrators to control everything from granular manipulation of critical security configuration through to virus database update schedules, file and vendor whitelisting, removable device control and power management.
Panoramic InsightThe CESM management console displays the global security status of the network and provides administrators with a ‘single-click' drilldown to those issues requiring immediate attention.
In panoramic mode, each endpoint is represented as a tile displaying 14 critical metrics which the administrator needs to quickly and accurately assess system status.
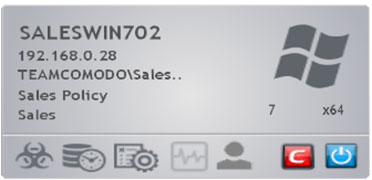
- Infection status
- Definition database status
- Security policy compliance
- System health status
- User assistance requests
- Security suite status
- Online status
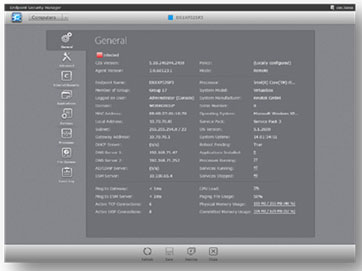 With the target endpoint(s) selected, the administrator is able to perform power operations, connect to the endpoint' s screen, modify the endpoint's group membership or applied policies, perform full or quick scans or drill even further down to the system's properties.
With the target endpoint(s) selected, the administrator is able to perform power operations, connect to the endpoint' s screen, modify the endpoint's group membership or applied policies, perform full or quick scans or drill even further down to the system's properties.
The endpoint properties informs administrators of critical network metrics, networking performance, hardware statistics, operating system and version, service pack, reboot status, count of installed applications, count of running processes and count of services. One click is all that is required to stop processes and services as well as browse and uninstall msi-based applications.